IP addresses list of hackers or malicious individuals
When it comes to cybercrime, you need to evaluate risks, establish strategies and implement solutions to stop hackers or intruders who seeks to destroy either your reputation or your systems.
1st step
You need both the right tools and knowledge or do business with a hosting company who has these qualities to identify and track down cybercriminals.
Step 2
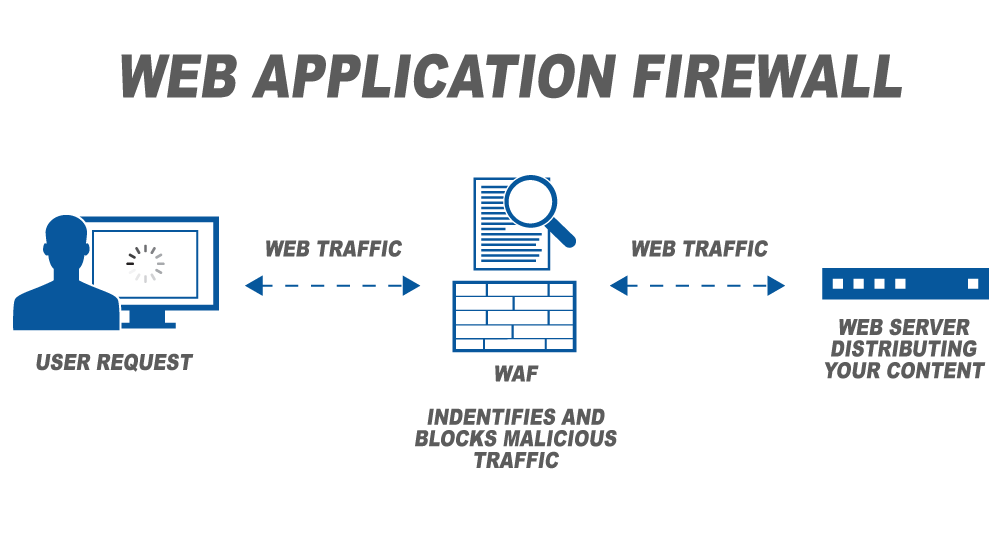
Block access of these individuals on your website. A good way to do this is to use .htaccess files, Web Application Firewall or tools against multiple authentication ( brute force )attacks like Fail2ban.
3rd step
File a complaint to the authority concerned. Most of the time the ISP provides an email address for cases of abuse. In last resort, after having the necessary evidence, speak directly to the police station in your neighborhood.
Updated list of IP addresses of malicious people
Internet Cloud Canada will create soon a section displaying the IP addresses of persons who abuse networks. In partnership with several network administrators, this list will be published on our website and enable you to act preventively against these individuals trying to break into your websites or abusing the network.
All of our customers are already protected and the list of IP addresses is immediately updated for them without having to do anything. It is our commitment to offer a healthy network with real statistics and maximum availability of your website here.
We also recommend to read our article of April 2015 by following this link. We show how to block users of the Tor network (Dark / Deep Web), who is recognized as people hiding themselves behind it to carry out their criminal actions.
November 2015 list
Until our section on Network Security is completed, here is the updated list for the month of November 2015. You can download the list here. The list is in the form of an .htaccess file. Simply edit the necessary parts for you.
Here is the list as presented in the file:
# BAN USER BY IP
<Limit GET POST>
order allow,deny
allow from all
deny from 193.201.227.158
deny from 66.187.75.245
deny from 130.185.82.32
deny from 217.78.30.163
deny from 84.240.9.6
deny from 209.90.88.137
deny from 188.165.118.117
deny from 179.61.12.103
deny from 72.34.34.33
deny from 5.196.18.168
deny from 142.4.4.201
deny from 192.99.100.176
deny from 198.57.164.33
deny from 162.144.85.112
deny from 154.50.0.75
deny from 142.4.4.201
deny from 72.34.34.33
deny from 199.201.110.60
deny from 198.1.76.21
deny from 162.144.85.112
deny from 45.55.241.251
deny from 207.20.232.240
deny from 178.32.53.94
deny from 80.82.64.92
deny from 89.248.169.36
deny from 75.127.118.226
deny from 144.172.233.238
deny from 74.124.214.251
deny from 72.34.62.48
deny from 93.174.141.54
deny from 198.1.71.253
deny from 37.187.77.154
deny from 184.170.151.20
deny from 211.9.64.2
</Limit>
All these IP addresses have done illegal actions on the networks lately. We advise you to block them immediately on your website.
Keep checking our website to discover our future section as well as updates to the list of IP addresses to ban.